
Silk Road became one of the most famous online black markets on the dark web for illegally selling drugs. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. The deep web is basically all the content that you can’t find using Google or Yahoo search. In addition, the content on the pages don’t need any special or custom configuration to access.
Data Breach Websites
Google doesn't index these sites, but other search engines do, including DuckDuckGo, and there are lists — including one run by Muffett — so you can find what you're looking for. "The Tor network is another network which sits on top of the TCP/IP internet, stitching the participating computers together into a wholly new network 'space', not IPv4, not IPv6, but 'Onion Space'." That central control allows for censorship, as by interrupting that lookup a site can effectively be banned from the web — this is why Turkish protesters were spraypainting IP addresses on walls in 2014, to tell others how to access Google directly without going via a DNS server. That may seem an extreme way to browse the web, but such protections are increasingly worth considering, says Sarah Jamie Lewis, executive director of the Open Privacy Research Society. The Tor browser is notorious for providing a secure browsing experience and allowing access to the d…
Minimize Or Rescale Your Tor Browsing Window
When used in unison, these tools seal the security and privacy vulnerabilities of the Tor network, keeping you anonymous as you roam the streets of the dark web. Dark web websites don’t bear Internet Corporation for Assigned Names and Numbers (ICANN) domains, such as .com. If the traffic passes through a Tor exit node run by a law enforcement agency, they will only see the IP address that the VPN assigned, not your real IP.
How To Access The Dark Web Safely And Anonymously
Tor routes data through at least three servers, and websites will only see the IP address of the last server, not yours. VPN services with a no-logs policy ensure that the service will not share any records of what you do online, and you don’t need to worry about stored data. So while normal addresses would end in .com or .org, Dark websites could have .onion, zip, etc. Always prioritize your safety, practice good cybersecurity habits, and use your judgment when interacting with the content and websites you encounter.
Surfshark works well with streaming platforms and is able to access geo-restricted content from the likes of Netflix, HBO, Hulu, and Disney+. The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a SHA512 authentication hash and 2048-bit DHE-RSA key exchange. It has a large network of secure servers, the ability to keep connections private, and apps that are rich in security features. In 2018, someone gained access to a third-party data center in Finland. While connected through NordVPN, your internet traffic is protected using AES 256-bit encryption.

How To Access The Dark Web – Complete Guide
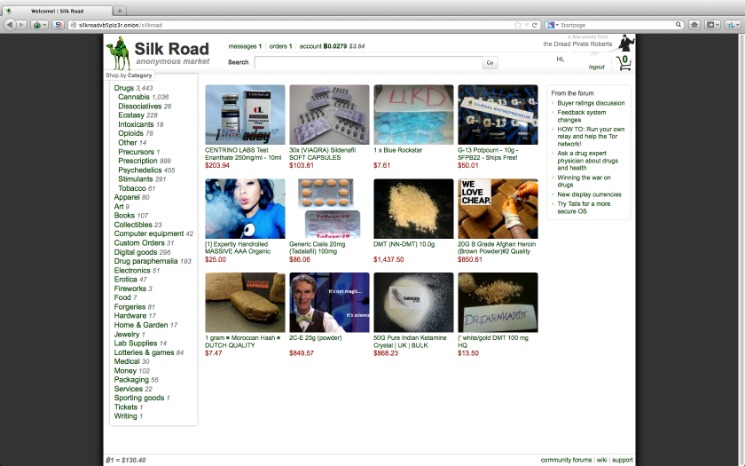
The legality of accessing the dark web depends on the activities conducted while on it. Simply accessing certain sites or engaging with the wrong links could implicate you in criminal investigations. Though it is not illegal to visit the dark web, accessing it can expose you to serious legal risks, even if you don’t have any criminal activity in mind.
Tips For Accessing The Dark Web

This means the VPN provider doesn’t see your real IP address and the VPN protects you from those bad exit nodes. Internet traffic first passes through the Tor Network, and then through the VPN. The exit node decrypts your traffic and thus can steal your personal information or inject malicious code. The final relay before your traffic goes to the destination website is known as the exit node.
Why Is Certified Ethical Hacker (CEH V13 AI) So Popular
Either way, some sites take up to a minute or more to load, so don’t fret. Copy the URL of the site you want to visit, press Enter, and you’re all set. If you’re prompted to connect, click the purple Connect button. The dashboard should open properly, indicating you’re ready to connect to any VPN server.

The dark web forms a small part of the deep web, but requires custom software in order to access its content. Such providers offer strong encryption and don’t store logs, ensuring all online footsteps are completely masked. What’s more alarming is the estimation that half of those visitors were connected to illicit activities.
After installing the Tor Browser, it’s important to configure it properly to ensure your anonymity and protect your online activities. No, as the Tor network is not good for torrenting — some Tor browsers block P2P traffic, and even Tor’s developers ask users not to use the network for P2P downloads. This encrypts your online traffic before entering the Tor network and shields your actual IP address.
- Fraud and scams run rampant on the dark web, including offers too good to be true and fake services requiring upfront payment.
- But because the dark web is poorly regulated, there’s a lot more illegal content on it, and accessing illegal content or services is still against the law.
- Here's everything you need to know about this other internet, as well as how to access it.
- Getting to the dark web is actually a lot easier than you might think—navigating it is a different story.
- Because the Tor network is run by volunteers, there’s also little in the way of accountability.
- Accessing the dark web sites isn’t safe and requires a user to go through several privacy measures to access it anonymously.
It is highly advisable to take all the necessary security measures discussed in this article to protect yourself. You can access the dark web using your Android device by following a few steps. Generally, it’s important to use Tor responsibly and in accordance with local laws and regulations. Many turn to the dark to grab such medications with their private and secure networks. Some common pain relievers and sleeping pills available in the EU are illegal in various Middle Eastern and Asia countries.
If your incoming traffic passes through a node run by cybercriminals, they could inject malware into the response code. Though most volunteers mean well, others are malicious actors and surveillance agencies. You can never be sure of the motive of the person operating the node that your traffic is routed through.



