
Torrenters can also make use of port forwarding, which allows connections to more peers in a torrent swarm. PrivateVPN allows torrenting and has dedicated servers in its home country for just that purpose. Internet traffic is secured using adjustable levels of encryption. Again, we don’t recommend this method, though it might be preferred if the security of Tor exit nodes is of concern. For its part, Mullvad says that it would “cease operation of our service” if forced by legal means to spy on users.

BBC Tor Mirror
It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications. The deep web is just the part of the internet you can’t find with a search engine. When you search for something on Google or Bing, you’re using the clear web. The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily. Then I’ll explain how to enter dark web websites.
Sites stored in the index are then ranked based on a variety of different factors, which is what decides how far up on the results page the sites appear in a search. This is the main way that search engines become aware of a certain website or web page, and is generally how sites like Google add web pages to their index. It does this through automated bots known as crawlers, which start out on websites already known to the search engine and visit every link on said websites before doing the same on the next site, and so on. In order to properly understand how the deep web works, you first have to understand a few fundamentals of how the regular internet operates, especially as it relates to search engines. Websites that exist purely on the deep web have different access, so there’s a level of privacy for the website hosts that isn’t possible on the regular internet.
Malicious Software
Unless you’re a fan of having big black SUVs parked outside your home and place of work, maybe only use Tor when you REALLY need to hide your online travels. If you need to protect or enhance your streaming, gaming, or torrenting activities, a Virtual Private Network (VPN) is a much better option as a secure connection to the net. This means Tor is a lousy option for streaming video, online gaming, or downloading files (torrenting). While this isn’t an issue for most of the trip (since each relay only has access to the previous and next relays in the network), it is an issue with the exit node.
How Tor Browser Works: Simplified Explanation
Dark web is usually used for illegal activities so you can’t only rely on the Tor browser and need a VPN for robust privacy and security. Conversely, the Darknet mode allows you to create restricted anonymity networks of people you only trust or know to share content with. It only accesses data uploaded on the Freenet, a P2P distribution datastore. The I2P network is a Tor-like anonymous network that can only be employed to access concealed services on the I2P system. A browser like Tor offers various features, including data security through layers of encryption, hiding your IP address, preventing online tracking, and much more.
- Even commerce sites that may have existed for a year or more can suddenly disappear if the owners decide to cash in and flee with the escrow money they’re holding on behalf of customers.
- That said, our detailed reviews follow a strict methodology that examines all relevant performance factors to help you arrive at your own informed conclusion.
- But it also provides a haven for cybercrime, illegal marketplaces, and other illicit activities.
- The dark web is home to the internet’s hidden sites, services, and products — some innocent, others downright dangerous.
Where Can I Find Safe Onion Links?

Threat actors also exploit vulnerabilities in your systems and software to gain access to them. The dark web, being a hub for criminal activities like identity theft and malware distribution, exposes you to various security threats like malware or phishing. Additionally, check the Block pop-up windows and Warn when websites try to install add-ons settings.
Downloadables
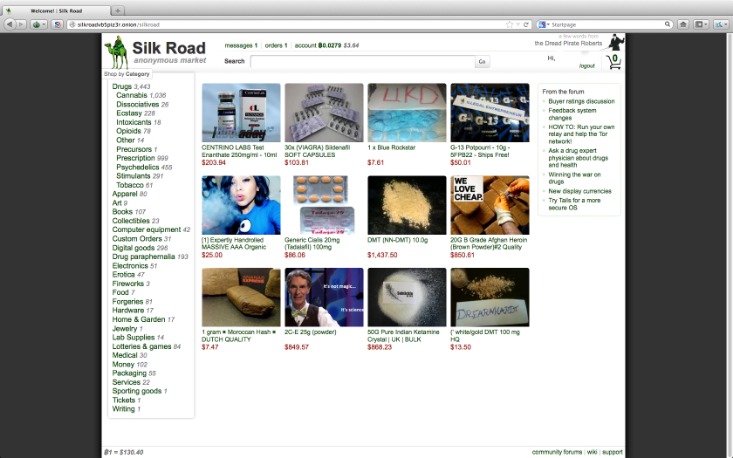
The indie game Sad Satan was claimed to have been found via the dark web, but inconsistencies in the reporting cast doubt on the story. This can lead to incrimination for other activities later in life. Even if a person does not make any purchases on illegal marketplaces like the Silk Road, custom software used by law officials can analyze activity and identify user identities. There is a significant risk that the government can target you for visiting a dark website, as many Tor-based sites have been taken over by police authorities worldwide. However, some of these alleged services, such as professional ‘hitmen,’ may be scams designed to defraud willing customers. You can find almost every kind of computer virus and malware on the dark web, which is why it’s a primary source for spreading these digital threats.

How To Access The Dark Web On An IPhone
The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content. First, let me explain that this article is intended for users who want to use the dark web for legal and needed purposes, such as finding censored news, blocked websites, and other much-needed services. Content includes non-indexed websites, apps, and resources, which can include protected information such as, online banking, specialized databases, non-linked and password-protected websites, and more. The dark web is web content that exists on darknets, which are overlay networks on the internet that require specialized software, configurations, and authorization to access. Such data includes medical records, financial information, research papers, private forums and networks, and other content. From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents.
It hosts encrypted websites, often used for privacy, anonymity, or illicit activities. On the other hand, the deep web is the hidden part of the Internet that contains private or restricted content that is not indexed by search engines. The surface web is the open part of the internet, which includes publicly accessible websites and resources.
It’s a misconception that everything on the dark web is illegal. It’s a collection of different sites and communities. Using a Virtual Private Network (VPN) adds an extra layer of security.
Verified Social Channels And News Sites
Even if they aren’t actively malicious, they might still have weak security or expose you to threats. The Tor Browser is the safest and most trusted way to access the dark web. By following some basic security tips and using the right tools, you can greatly reduce your chances of running into trouble.
However, it also supports legitimate uses like protecting free speech and accessing information in censored regions. The dark web often connotes illicit activities like illegal drug sales and hacking. Dark web monitoring tools are similar to a search engine (like Google) for the dark web. Finally, because the dark web routes all traffic through a series of proxy servers, which are operated by thousands of volunteers around the world, the search process is typically very slow. Another is the Invisible Internet Project (I2P), which specializes in the anonymous hosting of websites on the dark web. Users of the dark web should also realize that although their activity is technically anonymous, associating with people who are conducting illegal activities can have legal implications.
Be warned that this may cause some websites to not work properly. (And hackers are a big problem, especially on Dark Web websites. Read more about this in the “Words of Caution” section.) When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The dark web is a decentralized web, which means that the data is stored on many different servers around the world. It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims.



