
Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content. Instead, download Tor, the most secure and user-friendly option for accessing .onion sites. Instead, sites have complex .onion addresses, making them difficult to find without the exact URL.
Common Smartphone Mistakes You Should Avoid
These stolen email addresses are then sold or traded on the Dark Web, where cybercriminals can purchase them for various nefarious purposes. There are several reasons why your email address might end up on the Dark Web. It’s important to note that the Dark Web is just one part of the broader internet and should not be confused with the deep web. One such activity is the sale of personal information, including email addresses.
More Hidden Sites
Without these tools, neither Google nor any surface web browser can reach these secure, hidden parts of the internet. Tor, the most widely used, anonymizes traffic through layered encryption and random routing, providing a secure way to access dark web directories safely. Google’s business model depends heavily on tracking user behavior, collecting vast amounts of personal data to tailor ads and search results.
Abonnez-vous À La Newsletter Du Blog
- To access the dark web, you can’t use Google Search or browsers, such as Chrome or Safari.
- Browsing onion sites safely requires using the Tor Browser, which anonymizes your internet traffic.
- Avoid downloading files or clicking on unknown links, as this can expose you to various risks.
- The U.S. Army developed “onion routing” to protect intelligence communications online.
- This is also why the sites on the dark web are called Tor links.
- Meanwhile, Facebook also offers dark web access to their social network.
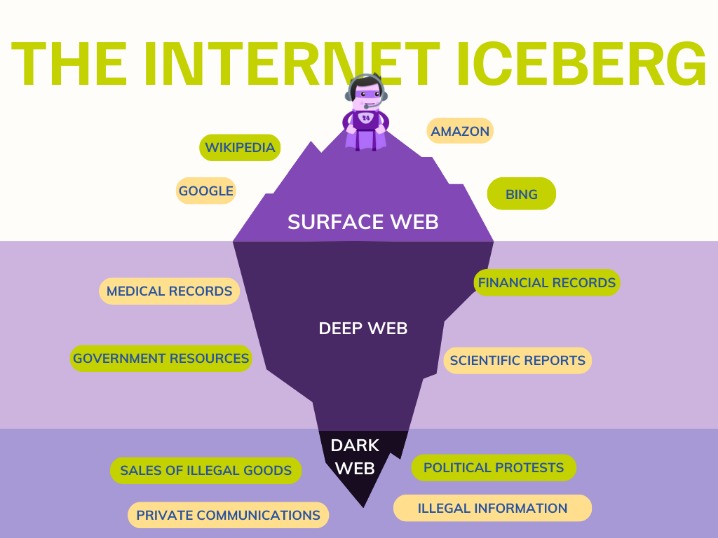
The Dark Web refers to a part of the internet that cannot be accessed through traditional search engines like Google, Bing, or Yahoo. I2P can only be used to access hidden sites that are only available on the I2P network. Your ISP can’t see which websites you’re visiting on the dark web when you’re using Tor, but they might be able to predict or assume you are using Tor if they analyze your monitored internet traffic. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content.
Guide Pour Accéder Aux Sites Onion
Use cryptocurrency to buy anything, and use a disposable email address for any type of communication on the dark web. While this is good advice for any type of web browsing, be particularly careful not to offer up any personal details, such as your credit card info or email address. As enticing as it might be, don’t follow links to other parts of the dark web. Check around with other users and ask if they know anything about the new marketplace.
Subscribe To The Blog Newsletter
A virtual private network (VPN) is a good way to mask Tor activities. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. This is because law enforcement often actively monitors these sites. The threat can extend to your entire network of devices connected to the internet.
Utiliser Onion Over VPN : Tout Ce Qu’il Faut Savoir
Well-known news websites, such as ProPublica, have launched deep websites. Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor. As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor.

This setup can help prevent network-level surveillance and reduce risks in environments where Tor use might be flagged or restricted. While the Tor Browser provides strong anonymity, using a VPN (Virtual Private Network) alongside it adds an extra layer of security and privacy. Daniel’s Hosting specializes in anonymous hosting services optimized for Tor sites, providing secure environments and DDoS mitigation. The ProtonMail Onion site offers the same encrypted email services trusted globally, now accessible anonymously through Tor. It hosts active discussions about market updates, hacking techniques, and security tips, with a community that actively moderates content to minimize scams.
This repository promotes responsible research and awareness. Hackers may use leaked email information to craft targeted phishing scams, aiming to trick victims into revealing more personal data or granting access to additional accounts. Fortunately, several tools and services can help you detect if your email address is found on the dark web.
Regularly updating your software and ensuring your operating system is patched are fundamental steps toward maintaining your cybersecurity. Always scrutinize the legitimacy of the sites you visit, particularly when dealing with sites cachés. It’s advisable to enable two-factor authentication whenever possible, adding an extra layer of protection to your accounts. Utilizing password managers can help generate and store complex passwords securely. Browsing safely requires a combination of good practices and an understanding of potential risks.
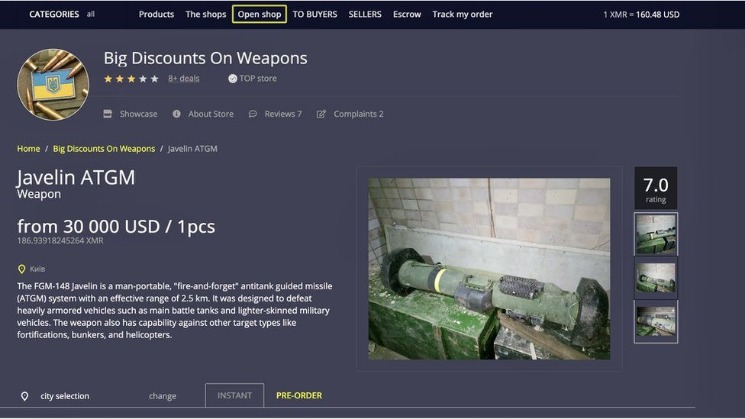
Awazon is a dark web marketplace that has quickly become popular for its anonymous e-commerce services. For example, it has a reputation for hosting pedophile sites. However, remember you must use the Tor browser to access them. You can choose the best darknet (.onion) website that suits you and start surfing. If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun.
Forums & Communities: Dread, The Hub, DarkNet Avengers
The Tor Browser looks and feels similar to a regular web browser but is configured to prioritize privacy and security by default. EscrowBay offers escrow services tailored to dark web transactions, holding funds securely until both buyer and seller confirm satisfaction, reducing fraud. BitBlender provides a mixing service that pools multiple users’ coins to anonymize their origins and destinations. The Wasabi Wallet is a Bitcoin wallet that uses CoinJoin mixing to obfuscate transaction trails, enhancing user anonymity. StrongBox adds advanced metadata stripping and encrypted messaging features, increasing whistleblower protection.



